Secure Private Access
Secure Private Access
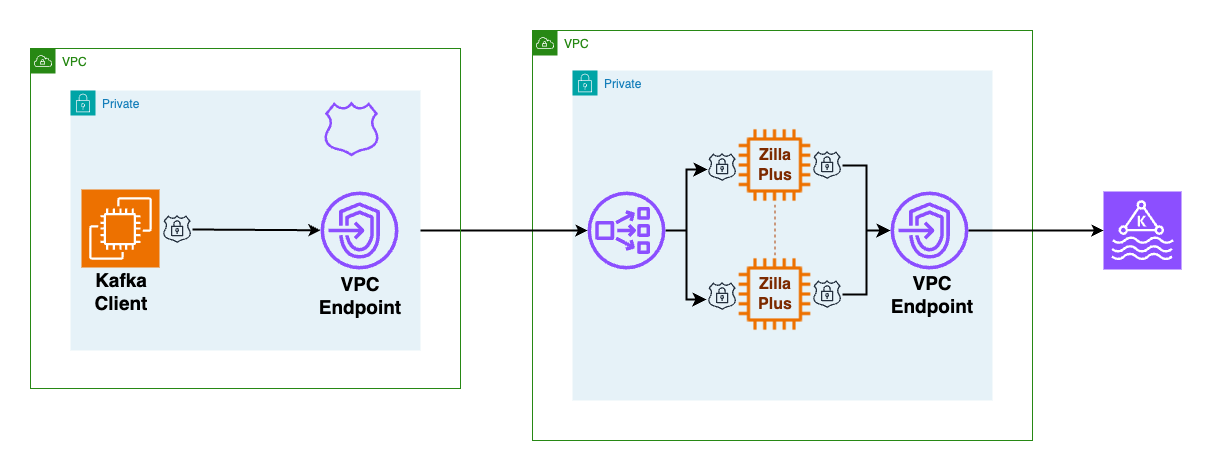
The Zilla Plus for Amazon MSK Secure Private Access proxy enables authorized Kafka clients deployed across cross-account VPCs to securely connect, publish messages, and subscribe to topics in your Amazon MSK Serverless cluster.
This setup establishes a fully private, secure, and scalable communication channel between Kafka clients and the Amazon MSK cluster by leveraging Zilla proxy.
Zilla: An auto-scaling, stateless proxy layer deployed in a private VPC that handles authentication and routing of Kafka requests.
Key Features
- Seamless MSK Serverless Connectivity across Cross-Account VPCs.
- No configuration changes required to the MSK cluster.
- Custom Wildcard DNS & Route 53 Hosted Zone Integration.
- Unified Domain Name for Kafka clients, streamlining configuration.
- Eliminates the need to manually whitelist each bootstrap endpoint to enable access.
- Seamless end-to-end TLS handshake.
- Auto-Scaling Zilla Instances.
- Deployed behind a Network Load Balancer for high availability and efficient request routing.
- Integrates with AWS Nitro Enclaves, enabling automated certificate renewal.
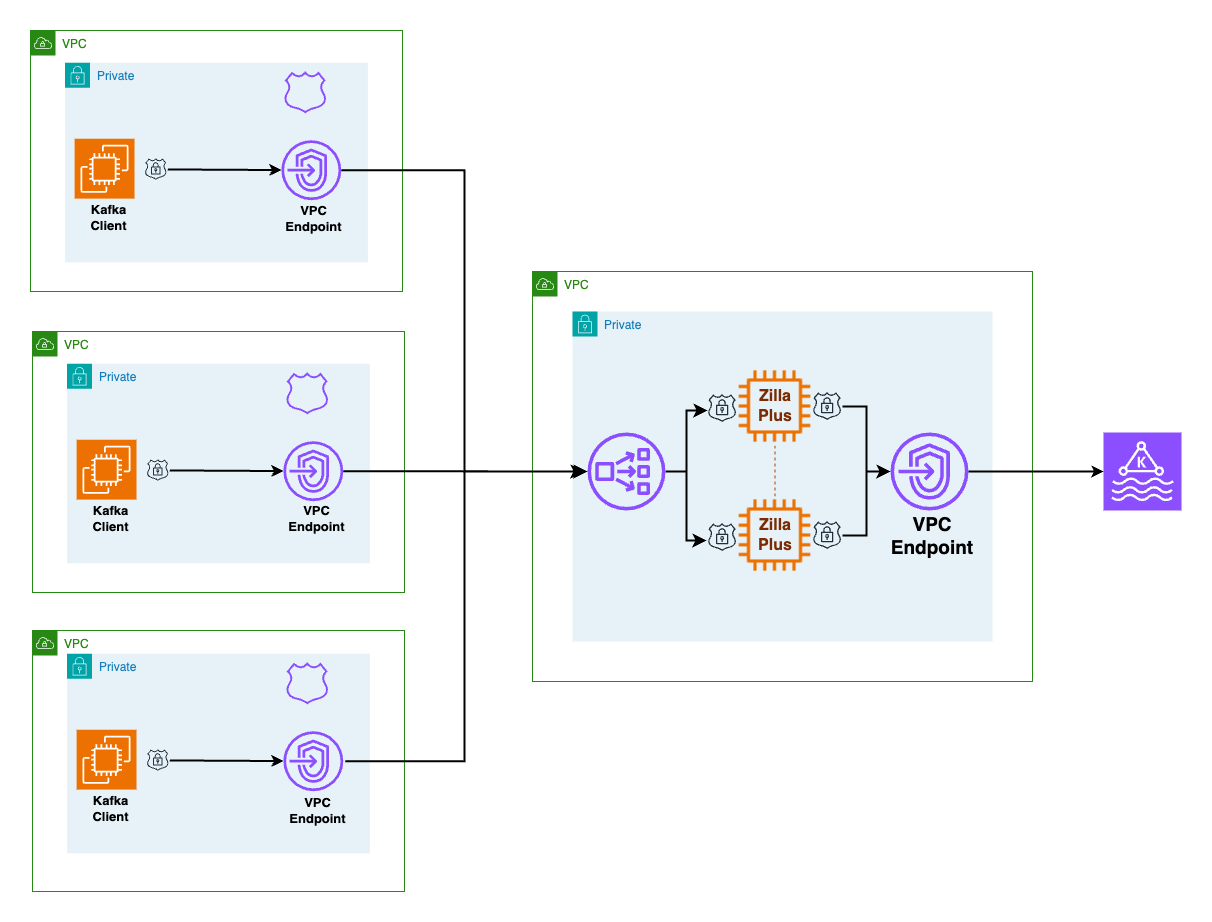
Many-to-One Private Access
Multiple Kafka clients from different cross-account VPCs securely connect to a single Amazon MSK Serverless cluster. This approach simplifies multi-tenant access and ensures a unified, private connectivity model.
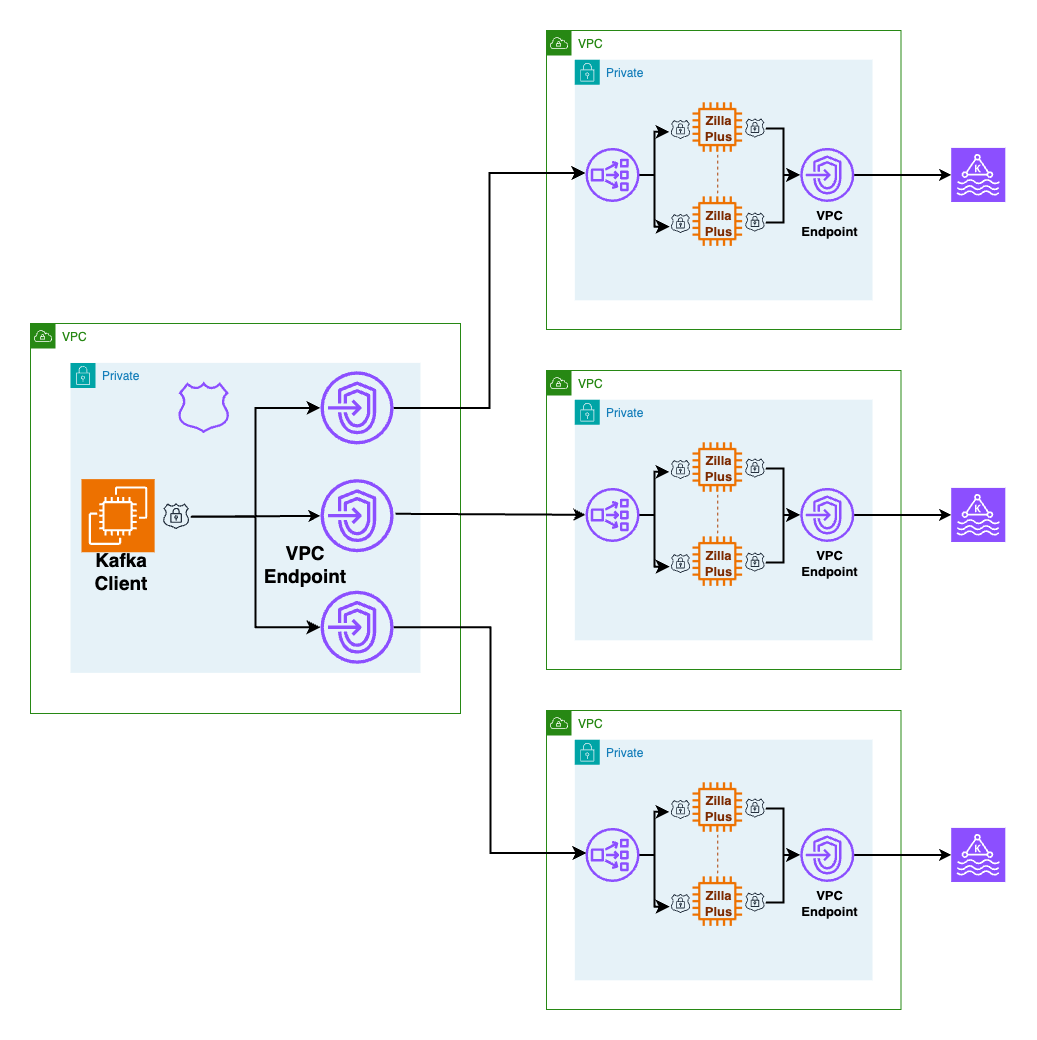
One-to-Many Private Access
Enables Kafka clients to securely access multiple Amazon MSK Serverless clusters deployed across different VPCs.
You will need to choose a wildcard DNS pattern to use for intranet access to the brokers in your Kafka cluster. These wildcard DNS names must resolve to the IP address of the VPC Endpoint in the client VPC, which then routes traffic via the VPC Endpoint Service to the ZillaPlus Network Load Balancer (NLB).
Additionally, the Zilla proxy must also be configured with a TLS server certificate representing the same wildcard DNS pattern.
Deploy with CDK
Follow the Secure Private Access with CDK guide to generate or deploy a custom AWS CDK stack.

